6 Best Authenticator Apps for 2024

Authenticator apps are increasing in adoption as they add another layer of security to user identity verification. A study found 90% of organizations reported identity-related breaches last year, and authenticator apps are designed to help reduce this number.
Authenticator apps help individuals and organizations double-check user identity by using two-factor or multi-factor authentication to verify and authenticate user identities before granting access to them.
In this article, we will review the best authenticator apps in 2024 and explore their features, pricing and pros and cons to help you decide the right authenticator app for your business.
Best authentication apps comparison
The table below shows the key features of these apps, their pricing and how they compare to each other.
| Software | Biometric authentication | Backup and recovery | Authentication type | Pricing |
|---|---|---|---|---|
| Google Authenticator | Yes | Yes | Time-based and counter-based codes. | Free |
| Microsoft Authenticator | Yes | Yes | Time-based codes, push notifications, biometrics. | Free |
| Twilio Authy | Yes | Yes | 2FA/MFA, OTP, soft tokens, push notification. | Starts at $0.05/ successful verification |
| Cisco Duo | Yes | Yes | 2FA/MFA, FIDO2 for anti-phishing. | Starts at $3/user/month |
| Yubico Security Key | Yes | Yes | 2FA/MFA, FIDO2 UF, touch/tap-and-go authentication using NFC or USB. | Contact vendor for quote. |
| FreeOTP | Yes | No (but available on FreeOTP+). | 2FA/MFA, push notification, hardware tokens, token-less authentication. | Free |
Google Authenticator: Best for secure offline authentication
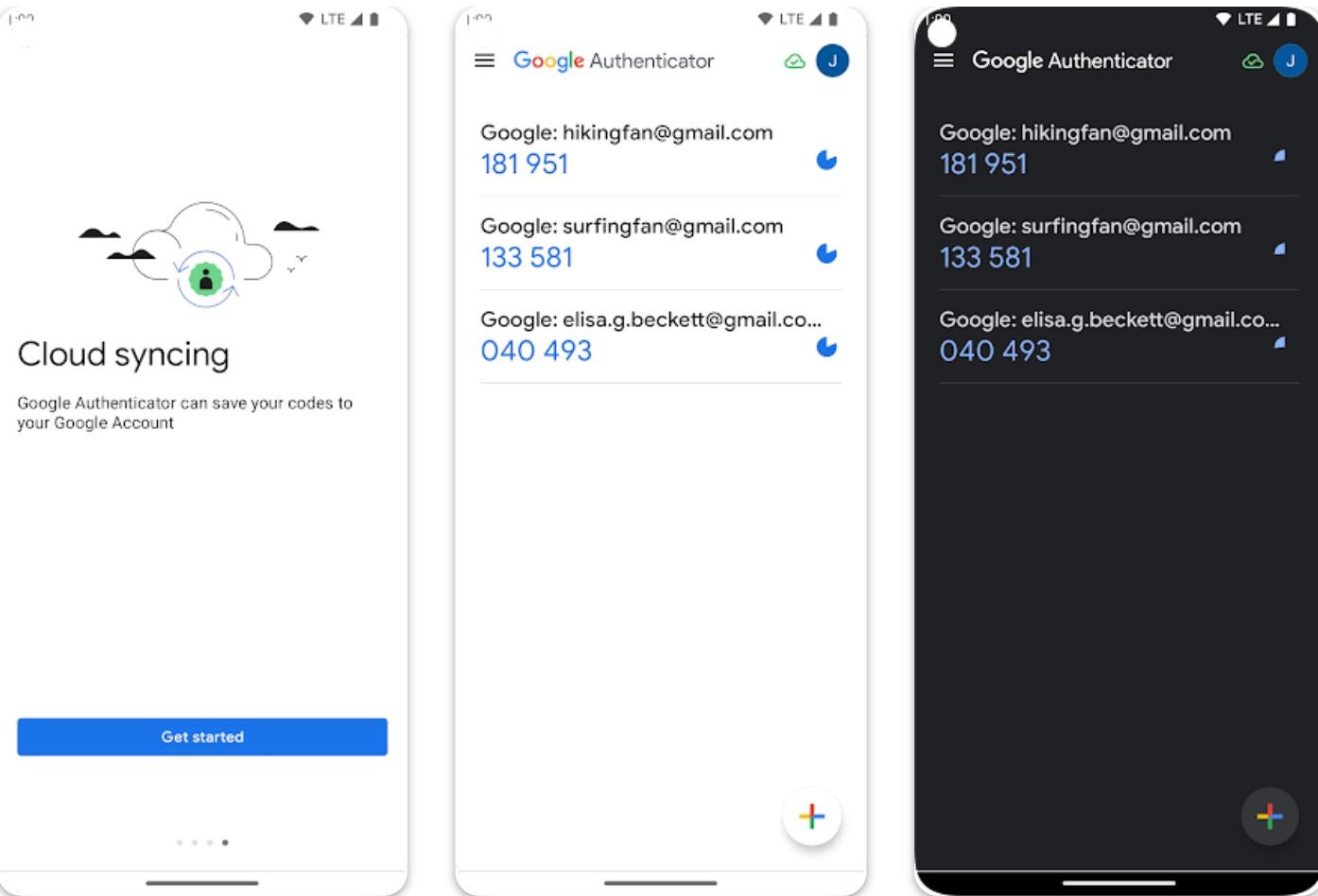
Google Authenticator is a multi-factor authentication app that generates unique, time-sensitive codes to enhance account security. The app works by generating time-based one-time passcodes that users enter in addition to their passwords when logging into their accounts. These passcodes are secure as they are generated locally (on the device) and not transmitted over the internet.
In 2023, Google Authenticator was updated to include backup capabilities through cloud syncing. However, users have reported issues with this feature.
Why we chose Google Authenticator
Google Authenticator made it to our list due to its offline authentication support through locally generated time-based passcodes.
Pricing
Application is free.
Features
- 2FA.
- Cross-platform compatibility.
- Time-based one-time password.
- Offline functionality.
- Multiple account management.
Pros
- The application is free.
- Has an easy-to-use interface.
- Offers locally generated passcodes for more security.
- It’s reliable as it doesn’t require an internet connection to function.
- Available for a wide range of users across diverse websites/platforms.
Cons
- Users have reported issues with cloud syncing feature.
Microsoft Authenticator: Best for biometric authentication

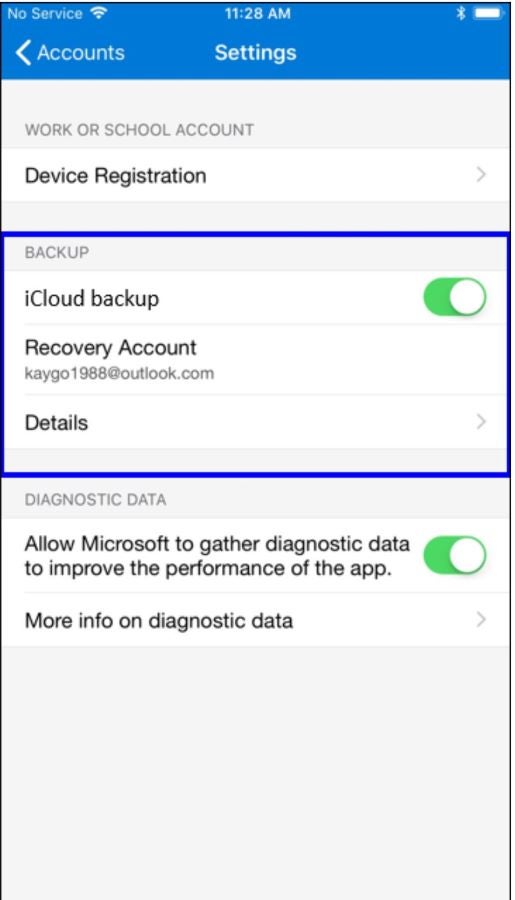
Microsoft Authenticator is another popular name in the authentication space. It is available to Microsoft, iOS and Android users and provides MFA through time-based codes, push notifications and biometrics. For enhanced security, you have the option to set up a PIN or use biometric verification to access the codes generated on your phone. The app also supports a password management feature that enables users to do things like accept verified IDs from organizations and save payment card details and addresses.
With Microsoft Authenticator, you can back up account credentials to the cloud, making it easier to restore them when you switch to a new device.
Why we chose Microsoft Authenticator
This authenticator was chosen for its flexibility displayed through its multiple authentication features such as PIN code, push notifications and biometric authentication for a seamless log-in experience.
Pricing
The application is free.
Features
- Push notifications.
- Password autofill.
- Biometric authentication.
- Cloud backup.
- Multiple account management.
Pros
- Supports a wide range of websites and services.
- The application is free.
- Provides MFA for easy access.
- Offers cloud backup and data recovery for lost devices or emergencies.
- Offers cross-device and cross-platform compatibility.
Cons
- Does not work offline.
- Push notifications can experience delays.
Twilio Authy: Best for cross-platform compatibility

Twilio Authy not only generates TOTP but also offers three other types of authentication: OTP, soft tokens and push authentication. It provides biometric authentication and multi-device functionality, enabling users to sync their 2FA tokens across new devices. This ensures easy access to accounts, regardless of which device is being used. Additionally, it allows users to deauthorize bad, stolen or retired devices for added security. Other notable features include an encrypted cloud backup and recovery, enhanced token protection with backup passwords, master passwords and PIN protection.
The app is available in both mobile and desktop versions.
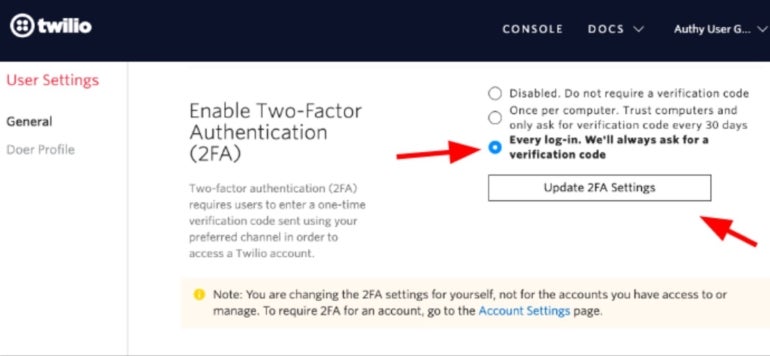
Why we chose Twilio Authy
This tool was selected for its versatility across devices and platforms for authentication and security, simplifying access to online accounts regardless of the device or platform used.
Pricing
Authy offers flexible, pay‑as‑you‑go pricing for multi‑channel user verification. Every successful verification is charged at $0.05. For a high-volume plan, contact the vendor for a quote.
Features
- Multi-device support.
- Encrypted cloud backup and recovery.
- Enhanced token protection with master passwords and PIN protection.
- Cross-platform compatibility.
- Push authentication.
Pros
- Offers offline accessibility.
- Provides three types of authentication.
- Offers multi-device synchronization.
- Has a mobile and desktop version.
- Provides encrypted cloud backup and recovery.
- Offers enhanced token protection.
Cons
- Having tokens on multiple devices and storing them in the cloud can be risky.
- Internet dependability may be limiting in emergency setups/sync.
Cisco Duo: Best for robust security features

Duo by Cisco is an easy-to-use cloud-based authenticator with a handy onboarding feature that enables new users to set up their accounts based on their security needs or priorities. It offers 2FA and MFA authentication and FIDO2 options for phishing-resistant authentication.
The desktop version (Duo Desktop) checks the health and security of endpoint devices with each authentication before providing access to protected applications and resources. Using the principles of zero trust, it provides IT teams with remote access to applications as well as adaptive access. The mobile version (Duo Mobile app) features a combination of location-based identity verification with push verification. This enables users to get a reading of their location before a log-in confirmation.
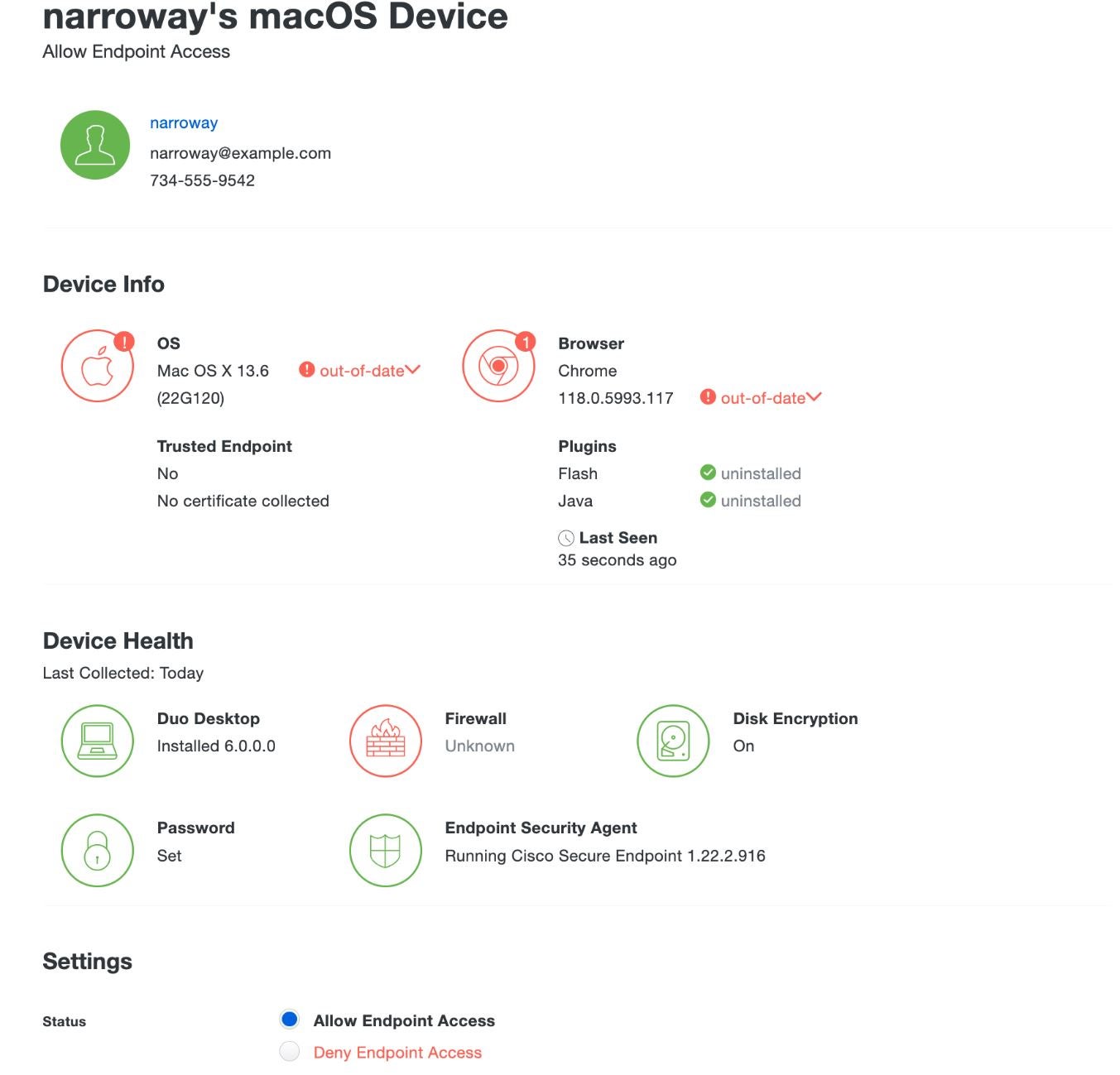
Why we chose Duo
Duo made it to our list because of its robust security features available in both the mobile and desktop versions.
Pricing
In addition to its free plan for up to 10 users (best for individuals or a small team), Duo offers a 30-day free trial and three paid subscriptions for medium to large enterprises:
- Duo Essentials: $3 per user per month.
- Duo Advantage: $6 per user per month.
- Duo Premier: $9 per user per month.
Features
- Duo Restore.
- Flexible multi-factor authentication.
- Remote and adaptive access.
- Single sign-on functionality.
- Duo Push.
Pros
- Offers location-based identity verification.
- Provides FIDO2 options for phishing attacks.
- Offers device health status tracking.
- Provides secure remote access for teams.
- Offers cloud backup and data restoration.
Cons
Yubico Authenticator: Best for hardware-based authentication

Yubico Authenticator enables users to generate 2FA codes on both mobile and desktop devices. One of its standout features is its hardware-backed authentication, which sets it apart from other authenticators. Unlike other authentication apps that store secrets on your phone or computer, Yubico Authenticator stores credentials in the YubiKey hardware security key. This means that even if you lose your phone or access to the Yubico Authenticator app, your credentials remain secure and cannot be extracted, ensuring that you won’t be locked out of your accounts. It also offers a seamless touch or tap-and-go authentication using Near Field Communication (NFC) and supports FIDO2/WebAuthn and FIDO U2F for user access protection.
The app is compatible with all major platforms, including Windows, macOS, Linux, iOS and Android, making it a versatile solution for users across different devices and operating systems. Worthy of mention is that the Yubico authenticator app is also compatible with other authentication apps using the smartcard certificates stored on the YubiKey.
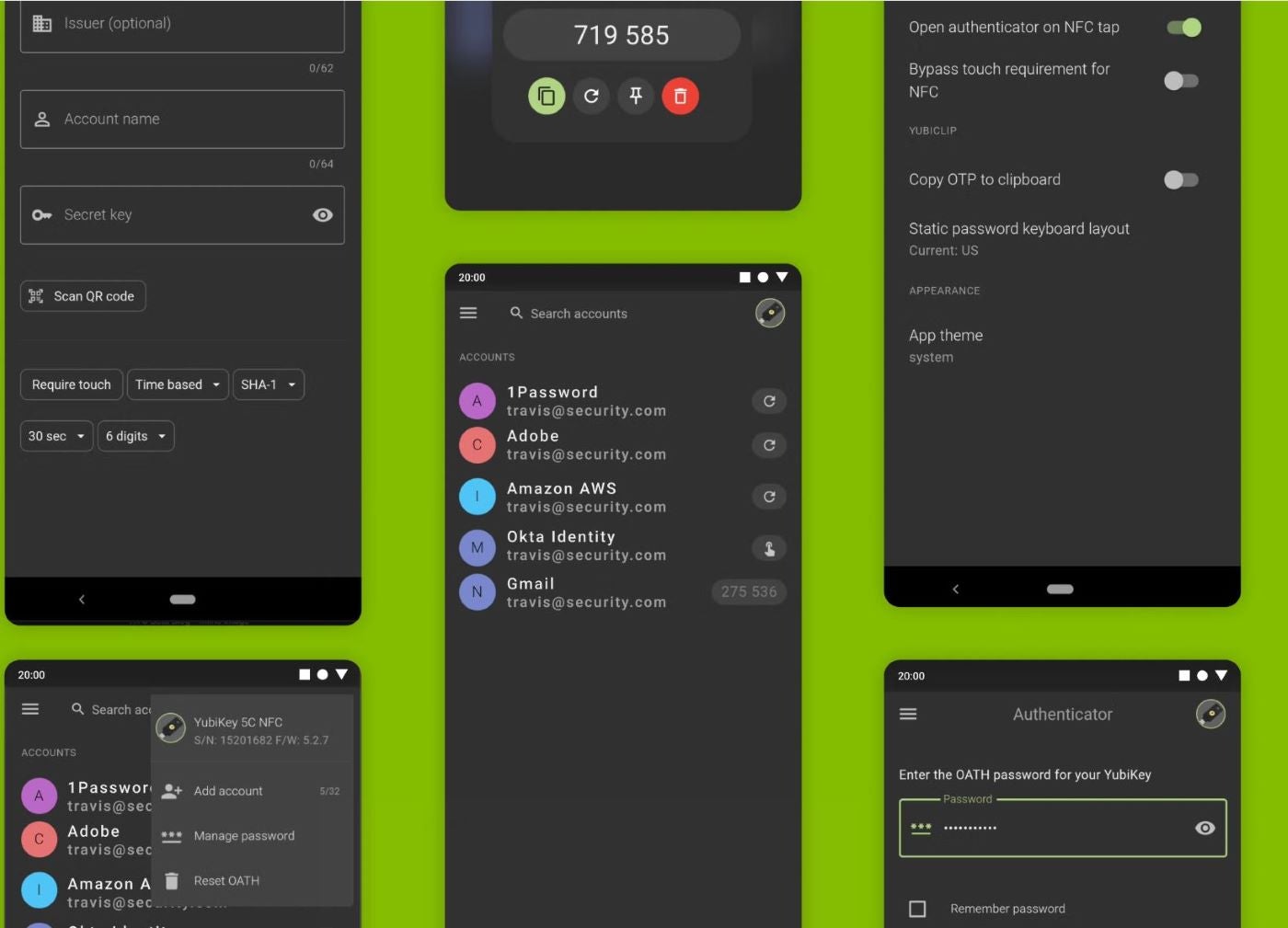
Why we chose Yubico
We chose Yubico for its rich hardware authentication features such as Yubico Security Key and touch authenticator using NFC or USB.
Pricing
Yubico offers YubiEnterprise Subscription, a monthly subscription-based tier for businesses with 500 users or more. Individuals and small to medium-sized businesses can purchase individual products based on their needs. For a quote, contact the vendor.
Features
- FIDO2/WebAuthn and FIDO U2F support.
- Physical security key.
- Touch or tap-and-go authentication with NFC or USB.
- Cross-platform compatibility.
- 2FA and MFA.
Pros
- Provides cross-platform coverage.
- Offers portable credentials across devices.
- Provides hardware-backed security.
- Supports FIDO2/WebAuthn and FIDO U2F for enhanced security.
- Offers one-touch authentication with USB/NFC support.
Cons
- The enterprise-ready security keys are exclusively available to YubiEnterprise Subscribers.
FreeOTP: Best for open-source authentication

FreeOTP is an open-source, enterprise-grade authentication solution whose repositories are constantly updated to enhance security. It provides various methods of authentication, including SMS, email, hardware tokens, mobile push notifications and tokenless authentication like QR code scanning. This authenticator integrates with several apps, services and protocols, making it suitable for different environments. In addition, it offers adaptive authentication that allows organizations to customize authentication policies tailored to meet their security needs based on user behavior and risk factors.
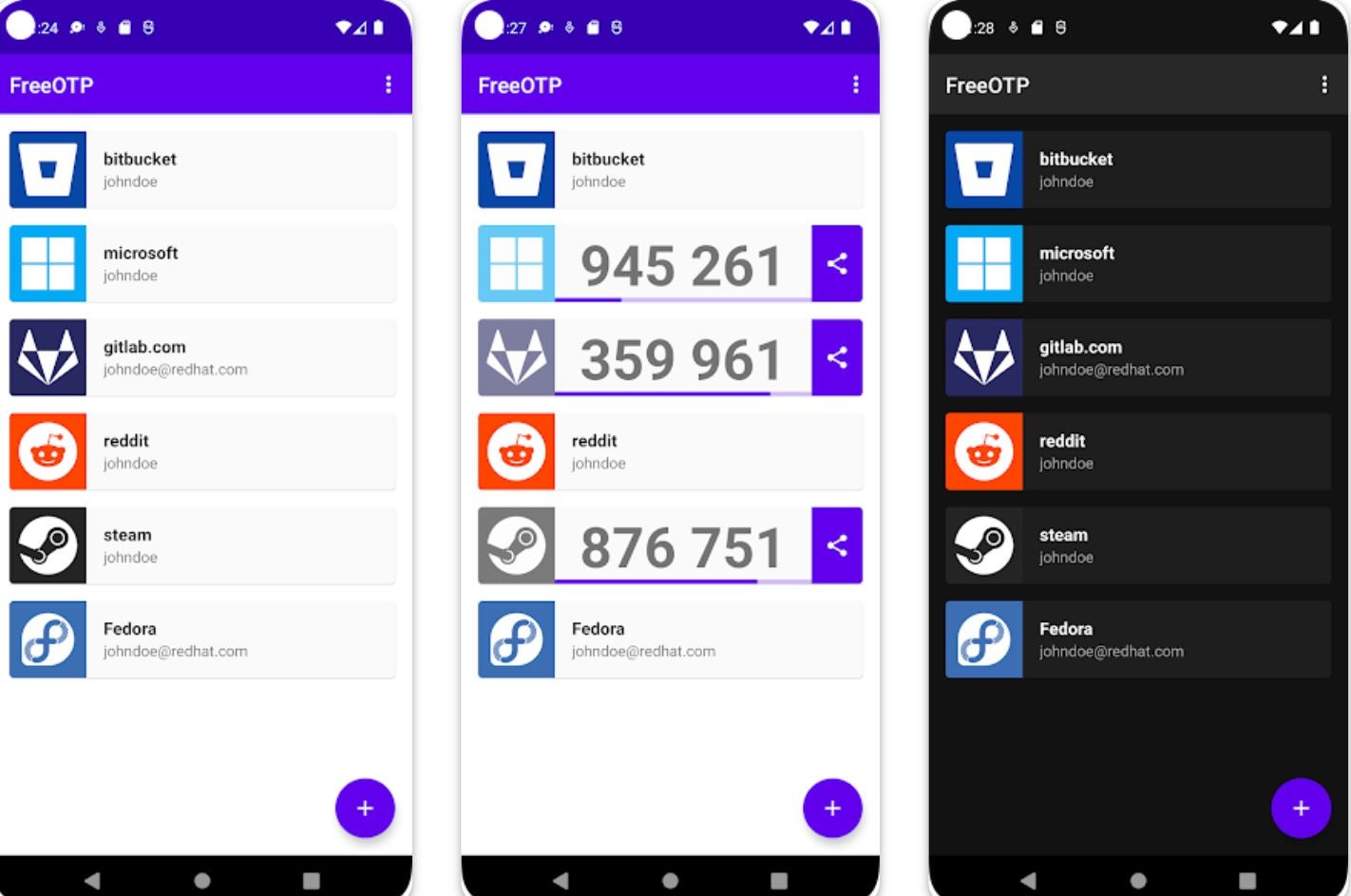
Why we chose FreeOTP
FreeOTP was chosen for its open-source nature that allows organizations to fine-tune it for specific use cases.
Pricing
This is a free-for-all tool.
Features
- Open-source software.
- TOTP.
- Tokenless authentication.
- Adaptive authentication.
- HMAC-based OTP.
- MFA.
Pros
- Offers integration with existing applications.
- Provides easy access in that it’s open-source.
- Application is free.
- Offers offline availability.
- Supports 2FA with TOTP and HOTP authentication.
Cons
- Its extensive features and customization options setup might be complex for new users.
How to choose the best authentication apps
In choosing an authentication app, organizations must take into consideration their size, existing structure, budget and specific security needs. For example, an organization with fewer than 500 employees would underutilize the YubiEnterprise Subscription because of its physical keys. If you need an authenticator app that offers different types of authentication and works on multiple devices simultaneously, you can opt for Authy. If your priority is an open-source authentication app for easy customization, you should consider FreeOTP. If you want to tilt toward a hardware authenticator or physical keys, then the Yubico Security Key is your best bet. Keep in mind that each of the reviewed authenticators delivers quality services, but each tool’s utility will depend on your authentication needs.
Methodology
For this review, I considered some key features of these solutions, focusing on their security details, accessibility and performance. Having obtained ample information from the vendors’ websites, I also checked for user feedback for the paid solutions. For firsthand experience, I reinstalled Google Authenticator and used it to power 2FA for my Twitter and Facebook accounts and also Microsoft Authenticator for my Outlook account. While it was quite easy to navigate the Google Authenticator with its simple interface and TOTP, security was tighter with Microsoft Authenticator as I needed to use biometrics to see the codes generated for each account log-in attempt and I also had to enter the code on the account seeking access.

